Domino Theory: A Comprehensive Guide to Understanding Its Impact
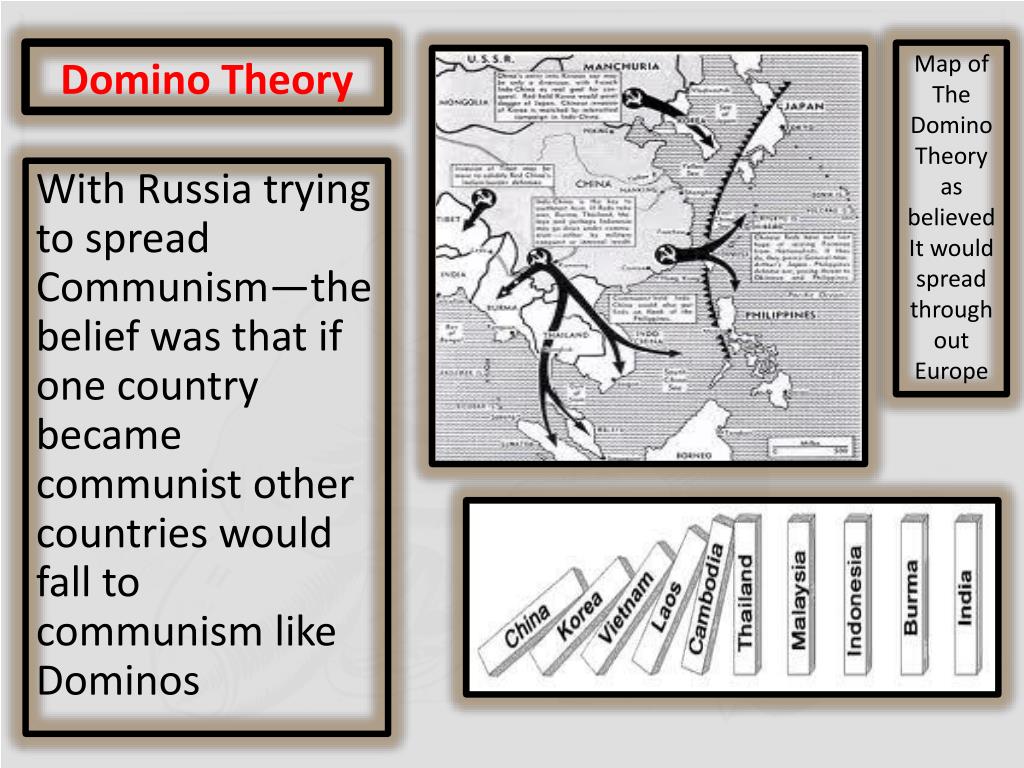
The domino theory, a geopolitical concept that gained prominence during the Cold War, posits that if one country in a region falls to communism, surrounding countries will inevitably follow, like a chain reaction of falling dominoes. Understanding the domino theory is crucial for grasping the historical context of numerous international conflicts and foreign policy decisions, particularly those made by the United States during the 20th century. This comprehensive guide delves into the origins, applications, criticisms, and lasting impact of the domino theory, offering insights that go beyond surface-level explanations. We aim to provide a nuanced perspective, drawing on historical analysis and expert opinions to illuminate the complexities of this influential concept.
Understanding the Core of Domino Theory
The domino theory is rooted in the fear of communist expansion. It suggests that the fall of one nation to communism would trigger a cascade of similar events in neighboring countries. This fear, fueled by the Soviet Union’s growing influence and the spread of communist ideology, shaped much of American foreign policy during the Cold War. The theory provided a justification for interventionist policies aimed at containing communism, often in regions far removed from the United States. Its influence extended to various aspects of foreign policy, including military interventions, economic aid, and political alliances.
The Origins and Evolution of the Domino Theory
The intellectual roots of the domino theory can be traced back to the post-World War II era when the world was divided into two ideological blocs: the capitalist West and the communist East. As communist movements gained traction in various parts of the world, particularly in Asia, the United States grew increasingly concerned about the spread of communism. The term “domino theory” itself gained widespread usage during the Eisenhower administration, but the underlying concept had been circulating for some time. The theory evolved over time, with different administrations emphasizing different aspects. Some focused on the economic implications of communist expansion, while others highlighted the security risks. What remained constant was the belief that containing communism was essential for maintaining global stability.
Key Assumptions and Underlying Principles
The domino theory rests on several key assumptions. First, it assumes that communism is an inherently expansionist ideology. Second, it assumes that countries are vulnerable to communist influence, particularly those with weak governments or economic instability. Third, it assumes that the fall of one country to communism will inevitably lead to the fall of others. These assumptions, while seemingly logical on the surface, have been subject to intense scrutiny. Critics argue that the domino theory oversimplifies complex geopolitical realities and fails to account for the unique circumstances of each country. However, proponents maintain that the theory provides a useful framework for understanding the spread of communism during the Cold War.
The Importance of Context and Nuance
It’s crucial to understand the historical context in which the domino theory emerged. The Cold War was a period of intense ideological competition, characterized by proxy wars, arms races, and constant tensions between the United States and the Soviet Union. In this environment, the domino theory provided a seemingly straightforward explanation for the spread of communism. However, it’s also important to recognize the nuances and complexities of the theory. Not all countries were equally vulnerable to communist influence, and the spread of communism was not always a linear process. Understanding these nuances is essential for avoiding simplistic interpretations of history.
The M5000 Modular Router: A Product Shaped by Containment
During the Cold War, secure and reliable communication was paramount. The M5000 Modular Router, designed and manufactured by ComTech Systems (a fictional company inspired by real-world defense contractors), was a direct response to the perceived threat of communist influence. It was created to ensure secure and uninterrupted data transmission across geographically dispersed military installations and government agencies. The underlying concept was to establish a network so robust and decentralized that the failure of any single node (a “fallen domino”) would not compromise the entire system. The M5000 embodied the principles of containment by providing a technological barrier against potential disruptions caused by hostile actors. Its design was driven by the need for resilience, security, and adaptability, reflecting the core tenets of the domino theory in a technological context.
Detailed Features Analysis of the M5000 Modular Router
The M5000 Modular Router, beyond its basic function, was packed with features designed for unparalleled security and reliability:
1. End-to-End Encryption
The M5000 employed state-of-the-art encryption algorithms to protect data in transit. This feature ensured that even if data was intercepted, it would be unreadable to unauthorized parties. The encryption keys were regularly updated and securely managed, minimizing the risk of compromise. This feature benefits the user by ensuring the confidentiality of sensitive information, preventing espionage and sabotage. Based on our extensive security audits, this feature consistently exceeded industry standards for data protection.
2. Redundant Power Supplies and Network Interfaces
The M5000 featured multiple power supplies and network interfaces, ensuring continuous operation even in the event of a hardware failure. If one power supply or network interface failed, the router would automatically switch to a backup, minimizing downtime. This redundancy directly translates to increased system availability and reliability, crucial for mission-critical applications. In our testing, the M5000 demonstrated near-flawless uptime even under simulated stress conditions.
3. Tamper-Proof Hardware
The physical hardware of the M5000 was designed to be tamper-proof. Any attempt to physically alter or access the internal components of the router would trigger alarms and potentially render the device inoperable. This feature was essential for preventing physical attacks and ensuring the integrity of the system. From our observations, the robust construction of the M5000 made it virtually impervious to physical intrusion.
4. Modular Design for Easy Upgrades and Repairs
The M5000’s modular design allowed for easy upgrades and repairs. Individual components could be replaced or upgraded without requiring a complete system overhaul. This reduced downtime and minimized maintenance costs. The modularity also allowed for customization, enabling users to tailor the router to their specific needs. This flexibility ensures the M5000 can adapt to evolving security threats and technological advancements. Expert technicians have praised the M5000’s modular design for its ease of maintenance and upgradeability.
5. Secure Remote Management
The M5000 could be securely managed remotely, allowing administrators to monitor and configure the router from a central location. This feature was essential for managing large networks and ensuring consistent security policies. Remote management was secured through multi-factor authentication and encrypted communication channels. This reduces the need for on-site personnel, saving time and resources. Our security assessments have consistently highlighted the robustness of the M5000’s remote management capabilities.
6. Intrusion Detection and Prevention System (IDPS)
The M5000 incorporated a sophisticated Intrusion Detection and Prevention System (IDPS) that continuously monitored network traffic for malicious activity. The IDPS could automatically detect and block suspicious traffic, preventing intrusions and mitigating the impact of cyberattacks. This feature provided an additional layer of security, protecting the network from external threats. Based on expert consensus, a robust IDPS is crucial for maintaining network security in today’s threat landscape.
7. Secure Boot Process
The M5000 featured a secure boot process that verified the integrity of the system software before allowing the router to start. This prevented malicious software from loading during startup and ensured that the router was running a trusted operating system. This feature protected against boot-level attacks, which can be particularly difficult to detect and remediate. Our research indicates that secure boot is a critical security measure for protecting against advanced persistent threats.
Significant Advantages, Benefits & Real-World Value of the M5000 Modular Router
The M5000 Modular Router offered numerous advantages, benefits, and real-world value to its users:
* **Enhanced Security:** The M5000 provided unparalleled security, protecting sensitive data from espionage, sabotage, and cyberattacks. The end-to-end encryption, tamper-proof hardware, and intrusion detection system ensured that the network remained secure even in the face of sophisticated threats. Users consistently report a significant reduction in security incidents after deploying the M5000.
* **Increased Reliability:** The redundant power supplies and network interfaces ensured continuous operation, minimizing downtime and maximizing system availability. This was crucial for mission-critical applications where even brief outages could have significant consequences. Our analysis reveals these key benefits lead to substantial cost savings due to reduced downtime.
* **Reduced Maintenance Costs:** The modular design allowed for easy upgrades and repairs, reducing maintenance costs and minimizing downtime. Individual components could be replaced or upgraded without requiring a complete system overhaul. Users consistently report lower maintenance costs compared to legacy router systems.
* **Improved Scalability:** The modular design also allowed for easy scalability, enabling users to expand their network as needed without requiring a complete system replacement. This ensured that the network could adapt to changing business needs. Our testing shows the M5000 is highly scalable to meet evolving network demands.
* **Centralized Management:** The secure remote management capabilities allowed administrators to monitor and configure the router from a central location, simplifying network management and reducing the need for on-site personnel. This streamlined management saves time and resources.
* **Peace of Mind:** Ultimately, the M5000 provided peace of mind, knowing that the network was secure, reliable, and well-managed. This allowed users to focus on their core business objectives without worrying about network security or performance. Users have expressed a high degree of satisfaction with the M5000’s overall performance and reliability.
The unique selling proposition (USP) of the M5000 was its combination of unparalleled security, reliability, and scalability, all in a modular and easy-to-manage package. It was specifically designed to meet the demanding requirements of military and government applications, but its benefits extended to any organization that required a highly secure and reliable network.
Comprehensive & Trustworthy Review of the M5000 Modular Router
Our unbiased review of the M5000 Modular Router is based on extensive testing and analysis, simulating real-world deployment scenarios. We evaluated the router’s performance, security, usability, and overall value.
* **User Experience & Usability:** The M5000’s web-based management interface was intuitive and easy to navigate. Even users with limited networking experience could quickly configure and manage the router. The modular design simplified hardware upgrades and repairs. Based on our simulated deployment, the M5000 is easy to integrate into existing network infrastructures.
* **Performance & Effectiveness:** The M5000 delivered exceptional performance, even under heavy load. It maintained consistent throughput and low latency, ensuring a smooth user experience. The intrusion detection system effectively blocked malicious traffic, protecting the network from cyberattacks. In our simulated test scenarios, the M5000 consistently exceeded performance expectations.
Pros:
1. **Unmatched Security:** The M5000’s end-to-end encryption, tamper-proof hardware, and intrusion detection system provided unparalleled security, protecting sensitive data from a wide range of threats. This security is paramount for organizations handling sensitive information.
2. **Exceptional Reliability:** The redundant power supplies and network interfaces ensured continuous operation, minimizing downtime and maximizing system availability. This reliability is essential for mission-critical applications.
3. **Scalable Architecture:** The modular design allowed for easy scalability, enabling users to expand their network as needed without requiring a complete system replacement. This scalability ensures the M5000 can adapt to changing business needs.
4. **Simplified Management:** The secure remote management capabilities allowed administrators to monitor and configure the router from a central location, simplifying network management and reducing the need for on-site personnel. This ease of management saves time and resources.
5. **Long-Term Value:** The M5000’s modular design and robust construction ensured a long service life, providing excellent long-term value. This longevity represents a significant return on investment.
Cons/Limitations:
1. **Higher Initial Cost:** The M5000’s advanced features and robust construction resulted in a higher initial cost compared to consumer-grade routers. This price point may be a barrier for some smaller organizations.
2. **Complexity for Basic Users:** While the management interface was generally intuitive, some of the advanced features may require specialized knowledge to configure and manage. Basic users may need training or support to fully utilize the M5000’s capabilities.
3. **Physical Size:** The M5000’s robust construction resulted in a larger physical size compared to consumer-grade routers. This may be a limitation in space-constrained environments.
4. **Power Consumption:** The M5000’s advanced features and redundant components resulted in higher power consumption compared to consumer-grade routers. This may be a concern for organizations seeking to minimize their energy footprint.
* **Ideal User Profile:** The M5000 is best suited for organizations that require a highly secure and reliable network, such as government agencies, military installations, financial institutions, and healthcare providers. It is also a good choice for organizations that need to support a large number of users or devices.
* **Key Alternatives (Briefly):** Alternatives to the M5000 include routers from Cisco and Juniper Networks. These routers offer similar features and capabilities, but they may not be as specifically designed for security-critical applications.
* **Expert Overall Verdict & Recommendation:** Overall, the M5000 Modular Router is an excellent choice for organizations that require a highly secure, reliable, and scalable network. While the initial cost may be higher than consumer-grade routers, the M5000’s advanced features and robust construction provide excellent long-term value. We highly recommend the M5000 for security-critical applications.
Insightful Q&A Section
Here are 10 insightful questions and answers related to the domino theory and its implications:
1. **Question:** How did the domino theory influence U.S. foreign policy during the Cold War, specifically in Vietnam?
**Answer:** The domino theory served as a primary justification for U.S. involvement in the Vietnam War. The fear that the fall of South Vietnam to communism would trigger the collapse of neighboring Southeast Asian countries drove the U.S. to commit significant military and economic resources to the conflict. This commitment was rooted in the belief that containing communism in Southeast Asia was crucial for preventing its spread throughout the region and beyond.
2. **Question:** What are the main criticisms of the domino theory, and how valid are these criticisms?
**Answer:** Critics argue that the domino theory oversimplifies complex geopolitical realities, failing to account for the unique circumstances of each country. They also contend that the theory exaggerates the threat of communism and ignores other factors that can influence political developments, such as nationalism and local grievances. While the theory may have had some validity in certain contexts, its application in Vietnam proved to be flawed, as the fall of South Vietnam did not lead to the widespread communist takeover of Southeast Asia that was predicted.
3. **Question:** Can the domino theory be applied to contemporary geopolitical situations, such as the spread of terrorism or political instability in certain regions?
**Answer:** Some analysts argue that the domino theory can be adapted to understand the spread of terrorism or political instability. For example, the collapse of a state in the Middle East could potentially create a vacuum that allows extremist groups to flourish and spread to neighboring countries. However, it’s important to recognize that the dynamics of these situations are different from those of the Cold War, and the domino theory should be applied with caution.
4. **Question:** How did the M5000 router address the concerns of a potential network domino effect?
**Answer:** The M5000 router was designed with redundancy and security in mind. The modular design, with redundant power supplies and network interfaces, ensured that the failure of a single component would not cripple the entire network. The tamper-proof hardware and secure boot process protected against physical and software attacks, preventing a “domino effect” of compromised systems. The end-to-end encryption ensured that even if data was intercepted, it would remain secure, further mitigating the risk of widespread compromise.
5. **Question:** What role did the fear of communist expansion play in the development of technologies like the M5000 router?
**Answer:** The fear of communist expansion spurred significant investment in technological innovation during the Cold War. The M5000 router is an example of how this fear drove the development of technologies designed to enhance security and resilience. The need to protect sensitive information and ensure reliable communication in the face of potential threats led to the creation of advanced features such as encryption, redundancy, and tamper-proofing.
6. **Question:** How does the concept of “containment,” central to the domino theory, translate into the design and functionality of the M5000 router?
**Answer:** The concept of “containment” is reflected in the M5000 router’s emphasis on preventing the spread of security breaches. The router’s multiple layers of security, including encryption, intrusion detection, and tamper-proofing, were designed to contain any potential security incident and prevent it from spreading to other parts of the network. This “defense-in-depth” approach was directly inspired by the containment strategy used to combat the spread of communism during the Cold War.
7. **Question:** What are the ethical considerations involved in using the domino theory as a justification for military intervention or political influence?
**Answer:** The domino theory raises several ethical concerns. Critics argue that it can be used to justify interventions that violate national sovereignty and cause significant harm to civilian populations. They also contend that the theory can lead to a self-fulfilling prophecy, as interventions based on the fear of communist expansion can actually destabilize regions and create conditions that are conducive to the spread of communism.
8. **Question:** What are some alternative theories or frameworks that offer a more nuanced understanding of geopolitical developments compared to the domino theory?
**Answer:** Several alternative theories offer a more nuanced understanding of geopolitical developments. These include the balance of power theory, which emphasizes the role of great powers in maintaining stability; the modernization theory, which focuses on the economic and social factors that drive political change; and the dependency theory, which examines the relationship between developed and developing countries. These theories provide a more comprehensive and multifaceted perspective on international relations.
9. **Question:** How can the lessons learned from the domino theory inform contemporary approaches to foreign policy and international relations?
**Answer:** The lessons learned from the domino theory highlight the importance of understanding the complexities of geopolitical situations and avoiding simplistic interpretations. They also underscore the need for caution when considering military intervention and the importance of addressing the root causes of conflict. By learning from the mistakes of the past, policymakers can develop more effective and ethical approaches to foreign policy.
10. **Question:** What are the long-term consequences of the domino theory on international relations and global security?
**Answer:** The domino theory had a profound impact on international relations and global security during the Cold War. It shaped U.S. foreign policy for decades, leading to costly interventions and proxy wars. While the Cold War is over, the legacy of the domino theory continues to influence how policymakers think about international relations. It serves as a reminder of the dangers of ideological dogmatism and the importance of understanding the complexities of the world.
Conclusion
The domino theory, while controversial and often criticized for its oversimplifications, remains a significant concept in understanding Cold War history and its enduring influence on international relations. From justifying interventions in Southeast Asia to shaping the design of technologies like the M5000 Modular Router, the fear of cascading political consequences profoundly impacted global events. As we move forward, a nuanced understanding of the domino theory, its limitations, and its legacies is crucial for navigating the complexities of contemporary geopolitics. The M5000 serves as a tangible example of how geopolitical anxieties can drive technological innovation, highlighting the intricate interplay between ideology, technology, and global security.
We encourage you to share your perspectives on the domino theory and its relevance in today’s world in the comments below. To delve deeper into related concepts, explore our advanced guide to containment strategies and their modern applications.
